Overview
During eDiscovery, a large number of ESI (electronically stored information) files may have to be shared among attorneys, paralegals, other support staff, and the opposing litigators themselves. Since the information in these files can be vital to the outcome of the case, attorneys must ensure these files’ availability, privacy, security, and integrity. In this post, we’ll take a look at the ideal conditions for file sharing during an eDiscovery process and then talk about why an MFT Server is the perfect tool for the job.

Much faster than email
When the size of ESI files to be shared are just a couple of Megabytes and when only 2 to 4 people have to share them, an email system may suffice. But when dealing with larger files or when the file sharing starts to involve more than a handful of people, then the limitations of email can make it a very inefficient tool.
One serious limitation in email is the size of its attachments. Most email services only support up to 25MB attachments. So if you want to send files that sum up to 1 GB – which if you want something to visualize on is really equivalent to one DVD – you’ll have to send those files in at least 40 batches. We’re not even considering the overhead that gets added to your actual file size upon attachment.
These days, a company’s relevant ESI can easily fill up an entire rack of DVDs. Aside from the usual data coming from spreadsheets, Word documents and a host of business applications, ESI now also includes data from Instant Messaging, voice mail, email, text messages and social media (e.g. LinkedIn, Facebook, Twitter) posts.
Thus, if you insist on using email, you’ll have to labor through hundreds of batches. Clearly, this can be a very time-consuming exercise. And we’re not even talking about large enterprises, which deal with tera bytes of ESI.
Since we’ve mentioned DVDs, it’s interesting to note that some law firms still do burn ESI files on to DVDs and send them through courier. But I don’t think we need to go through how slow that particular method can be in comparison, do we?
Looks like the perfect job for an FTP service then, right? Wrong.
Secures confidential information
Sure, it’s much easier to share large volumes of files using an FTP server. There’s no need to send in batches. You can share everything in one go. You can even create directories remotely on the server and segregate files as needed.
The problem is that FTP by default is not secure. Since these ESI exchanges can include sensitive data like personal information, trade secrets, financial information, salaries of key personnel, and so on, it is imperative that you choose a secure file transfer protocol that can preserve the confidentiality of your data as it gets transmitted over insecure networks like the Internet.
If these types of information fall into the wrong hands (e.g. corporates spies, identity thieves, or even the general public), it can harm the party who owns them and damage your reputation as a trusted counsel. Secondly, certain types of information are protected by laws/regulations. If you don’t implement security measures during eDiscovery, you could be found violating those regulations.
For instance, if your client is covered by HIPAA and your eDiscovery process involves ePHI (electronic protected health information), you should adhere to certain standards of security that are compliant to HIPAA. Otherwise, you might be held accountable if a data breach ensues and you’re found to have been negligent in protecting the ePHI in question.
HIPAA isn’t the only piece of legislation you should be concerned about. There are other laws/regulations like PCI DSS, GLBA, and certain state data breach notification laws which likewise protect certain types of ESI and hence can impact your eDiscovery exchanges as well.
One way of protecting sensitive information is by replacing FTP with secure file transfer protocols like FTPS and SFTP. These network technologies are capable of encrypting ESI and protecting them as they are sent through insecure networks. As soon as they arrive at the server, you can then provide data-at-rest protection through a suitable encryption technology such as OpenPGP.
These data-at-rest and data-in-motion encryption technologies are normally supported by a managed file transfer server.
Comprehensive access control
Most eDiscovery processes involve multiple individuals; e.g. members of your legal team, paralegals, IT specialists, forensic investigators, and members of the opposing counsel. It might be practical to use a single server for sharing ESI among all these individuals. However, not everyone needs to have access to exactly the same set of information.
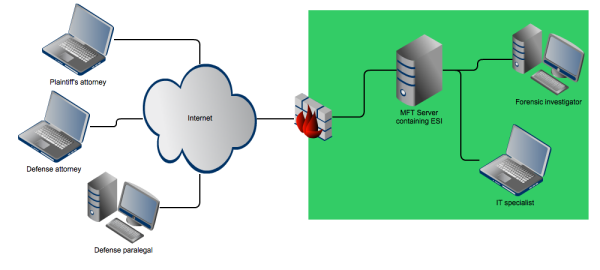
For instance, IT specialists, forensic investigators and paralegals on your side might have to be given access to raw data in native format that have been freshly extractedfrom your client’s systems. Members of the opposing counsel, on the other hand, might only need to have access to a smaller subset of this data; in particular those that have already undergone culling and perhaps transformed into image formats like PDF or TIFF.
If this is the case, you might want to segregate these different sets of information and grant certain groups of people access only to specific sets. To help you realize that, your server should have some kind of grouping mechanism as well as a flexible authorization feature that would allow you to assign different levels of authorization and access to different people.
Additionally, you might want to keep track of the file transfer activities of everyone who has access to the server so that if something goes wrong, you will know who can be held accountable. This can be achieved by using a server that supports detailed logging.
Again, one solution designed to satisfy the conditions mentioned in this section is a managed file transfer server. A managed file transfer server would already include a comprehensive selection of access control features that can readily support strong implementations of authorization, authentication, and accountability principles.
Automated file transfers
Large volume file transfers can clog your network. Thus, when exchanging relevant ESI with people involved in the eDiscovery process, it would be wise to upload/download during off-peak hours; for example, at night. That way, the files will be ready for review first thing in the morning.
A managed file transfer system that supports automated uploads and downloads can be a big help in this regard. You simply set an upload/download schedule and the server will automatically perform the upload/download at the scheduled time. I’m pretty sure you’ll find that more convenient than sending email attachments in numerous batches.
Some MFT Servers even support triggers that enable automatic sending of email notifications or tweets to specific members of your legal team (or even those of the opposing counsel) when certain conditions are met. For instance, notifications can be sent when an upload is complete, when a virus is detected, or when an error occurred.
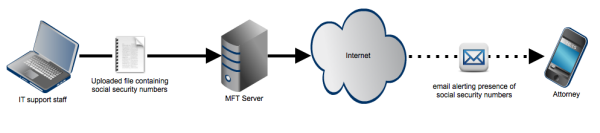
Notifications may also be sent when certain keywords or patterns of characters (e.g. credit card, bank account, or social security numbers) are found within the uploaded files. This can be useful in instances when you want to be notified whenever sensitive data are found.
Another automated feature that can be very useful when sharing ESI is auto-encryption of uploaded files. This will ensure the security of each uploaded ESI file while it is stored on the server.
Conclusion
The best tool for sharing ESI files in an eDiscovery process is an MFT Server. Aside from possessing the same speed and usability characteristics as a regular FTP server, a managed file transfer server also offers superior levels of security and automation. It even supports advanced access control features. The easiest way to appreciate what we’re saying is to try our free evaluation version of JSCAPE MFT Server. Give it a test run and see why it’s perfect for eDiscovery.





