Overview: What Is AES?
First adopted by the U.S. government to protect classified information, Advanced Encryption Standard (AES) has long gained global acceptance and is used for securing sensitive data in various industries. In this post, we’ll discuss AES encryption and explain its vital role in securing sensitive files sent over the Internet.

What Is AES Encryption?
AES is a cipher, a method for encrypting and decrypting information. Whenever you transmit files over secure file transfer protocols like HTTPS, FTPS, SFTP, WebDAVS, OFTP, or AS2, there’s a good chance your data will be encrypted by some flavor of AES ciphers — either AES 256, 192, or 128. We’ll discuss more about these AES encryptions shortly.
Different secure managed file transfer software may be equipped with varying selections of encryption algorithms. Some ciphers may be included in certain selections but absent in others. Not AES. AES will almost always be present in all but a few. Why is this so? It all started when the US government began looking for a new encryption algorithm that could be used to protect sensitive data.
How Rijndael Became A Standard
For about two decades since 1977, the US government used a cipher called DES (Data Encryption Standard) to protect sensitive, unclassified information. Unfortunately, that cipher was later proven to be insecure, prompting the government to look for a replacement.
This led to a standardization process that attracted 15 competing encryption designs, which included — among others — MARS from IBM, RC6 from RSA Security, Serpent, Twofish, and Rijndeal. It was Rijndael, designed by two Belgian cryptographers (Joan Daemen and Vincent Rijmen), that eventually became the standard and is known as Advanced Encryption Standard or AES.
The selection process was very stringent, taking five years to complete. During that span, many experts from the cryptographic community carried out detailed tests and painstaking discussions to find vulnerabilities and weaknesses. The participation of different sectors, which showed the openness of the selection process, speaks volumes of how credible the process was.
Although the cipher’s strength against various attacks was a major consideration in choosing the standard, it included other factors like speed, versatility, and computational requirements. The government wanted an encryption standard that wasn’t just strong, but also fast, reliable and easily implemented in both software and hardware — even those with limited CPU and memory.
Although the other encryption algorithms were also very good, the Rijndael cipher was ultimately selected and declared a Federal Information Processing Standards or FIPS standard by the NIST (National Institute of Standards and Technology) in 2001. It was approved by the Secretary of Commerce and then recognized as a federal government standard the following year.
Note: The official AES standard is specified in FIPS PUB 197.
The rise of AES didn’t end there. In 2003, the government deemed it suitable for protecting classified information. The NSA (National Security Agency) is still using AES to encrypt Top Secret information.
This is why AES has gained the confidence of various industries. If it’s good enough for the NSA, then it must be good enough for businesses. Let us show you how your business would benefit, through this free trial and conversation with our account manager.

Let’s Get A Little Bit More Technical
So, how does AES work? AES belongs to a family of ciphers known as block ciphers. A block cipher is an algorithm that encrypts data on a per-block basis. The size of each block is usually measured in bits. AES, for example, is 128 bits long. Meaning, AES will operate on 128 bits of plaintext to produce 128 bits of ciphertext.
Like almost all modern encryption algorithms, AES requires the use of secret keys during the encryption and decrypt processes. AES supports three keys with different key lengths: 128-bit key, 192-bit keys, and 256-bit keys. The key size is also important. The longer the key, the stronger the encryption. So, AES 128 encryption is the weakest, while AES 256 encryption is the strongest.
In terms of performance though, shorter keys result in faster encryption times compared to longer keys. So 128 bit AES encryption is faster than AES 256 bit encryption.
The keys used in AES encryption are the same keys used in AES decryption. When the same keys are used during both encryption and decryption, the algorithm is said to be symmetric. Read the article Symmetric vs Asymmetric Encryption if you want to know the difference between the two.
How Is The AES Encryption Algorithm Used In Secure File Transfers?
As mentioned earlier, AES is implemented in secure file transfer protocols like FTPS, HTTPS, SFTP, AS2, WebDAVS, and OFTP. But what exactly is its role?
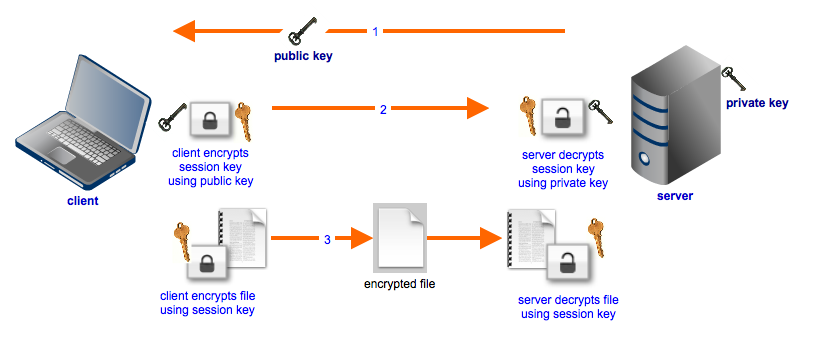
Because symmetric and asymmetric encryption algorithms each have their own strengths, modern secure file transfer protocols normally use a combination of the two. Asymmetric key ciphers, like public key encryption algorithms, are great for key distribution and are used to encrypt the session key used for symmetric encryption.
Symmetric key ciphers like AES are more suitable for encrypting the actual data (and commands) because they require less resources and are also much faster than asymmetric ciphers. The article Symmetric vs Asymmetric Encryption has a more thorough discussion regarding these two groups of ciphers.
Here’s a simplified diagram illustrating the encryption process during a typical secure file transfer secured by SSL/TLS (HTTPS, FTPS, WebDAVS) or SSH (SFTP). AES encryption operates in step 3.
Get Your Free Trial
Would you like to try this yourself? JSCAPE MFT Server is platform-agnostic and can be installed on Microsoft Windows, Linux, Mac OS X and Solaris, and can handle any file transfer protocol as well as multiple protocols from a single server. Additionally, JSCAPE enables you to handle any file type, including batch files and XML. Complete a short form for your trial of JSCAPE MFT Server now.
Request your free JSCAPE MFT Server Trial
Related Content
- How To Set Up A HTTPS File Transfer: HTTPS File Sharing
- What Is AS2 Protocol? How To Use Applicability Statement 2
- What Is HMAC And How Does It Secure File Transfers?
- What Is HTTP Strict Transport Security (HSTS)?
Frequently Asked Questions
What does AES Stand for?
AES stands for Advanced Encryption Standard. It was first used by the US government to protect classified information. Since then, it has gained global acceptance and is used for securing sensitive data in various industries. AES is what is known as a cipher, which is a method for encrypting and decrypting information.
Learn more about Ciphers and how they are used in encryption
Why do you need AES Encryption?
You need AES encryption to protect electronic data. AES protects data by encrypting it with a cryptographic algorithm. AES is a symmetric block cipher that first encrypts data into ciphertext, which is unreadable and unintelligible. Then, it decrypts the data back to its original form, known as plaintext.
When do you use AES in File Transfers?
AES is commonly used in secure file transfer protocols like FTPS, HTTPS, SFTP, and others. AES is a symmetric key cipher, which is good for encrypting the data being transferred, and the commands being sent between the servers. AES is generally faster and uses less resources than an asymmetric key cipher like a public key encryption algorithm.





