There are a number of things to consider when setting up the reverse proxy and firewalls in your DMZ. These things are going to have a significant impact on the performance and security not only on your file transfers but for your entire network in general, so you really need to weigh the advantages and disadvantages of each set up before deciding how you are going to put everything together. Let’s talk about it when you request a free trial.
Effects of implementing NAT
Implementing NAT (Network Address Translation) on your firewalls might seem like a good way to improve security in your DMZ and internal network. For example, by referencing your hosts (including your reverse proxy) using static NAT, you can make it difficult for a potential attacker to obtain vital information about your DMZ and internal network’s infrastructure.
However, NAT also has a couple of disadvantages. Ironically, one of those disadvantages has something to do with security. You see, NAT cannot get along well with some encryption technologies. This is because NAT works by making certain changes to data packets. Specifically, it changes IP addresses and checksums. But if the packet is encrypted, NAT may not be able to do what it’s supposed to do.
Another disadvantage of NAT is that it can contribute to latency, which can slow down your file transfers. There are two instances in a NAT process that can add to latency: 1) When it looks up the NAT table for a match and 2) When it modifies the packet to perform the address translation.
Lastly, NAT can have problems with protocols like FTP and FTPS, which use more than one connection. You’ll have more success if you use SFTP. If you want a more thorough explanation regarding the issues between FTP and firewalls, please read the article Active vs Passive FTP Simplified.
What firewall architecture should you use?
There are two common firewall architectures to choose from. One is the single-firewall architecture, while the other is the dual-firewall architecture.
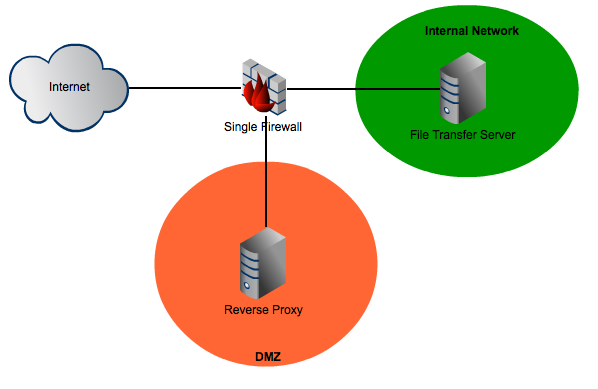
Single Firewall Architecture
Dual Firewall Architecture
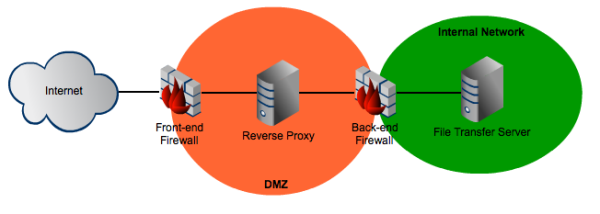
Obviously, the dual-firewall architecture is going to be more expensive and more complex to manage. The main advantage it offers is that, if the two firewalls are from different vendors and of different models, it would be more difficult for an attacker to break into your internal network.
Each firewall would have its own pecularities and technicalities, thus any person who would like to break through would have to be adept at two different sets of attack methods.
How should you set your DMZ firewall rules?
Regardless which architecture you want to use, you should make sure your DMZ firewall(s) and your reverse proxy are configured to work together. Ideally, firewall rules meant to control relevant traffic flowing from the Internet to the DMZ should be configured in such a way that they would all flow into the reverse proxy.
Your DMZ reverse proxy could then be set to allow only certain protocols to pass through and to connect to specific hosts in your internal network. With this configuration, the reverse proxy would serve as a single point of access to those internal hosts and thus make security implementation easier.
Lastly, firewall rules meant for traffic flowing from the DMZ to your internal network should be configured in such a way that only traffic coming from the reverse proxy and directed at certain servers in your internal network are allowed to pass through. All other packets must be rejected.
Here’s a simplified diagram of the ideal traffic flow.
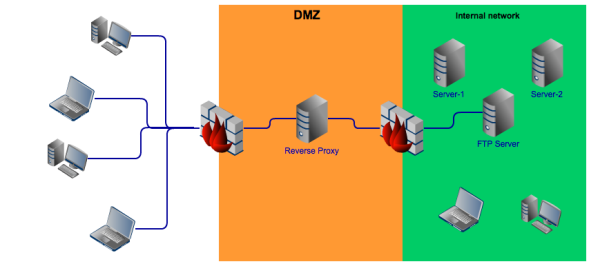
Summary
In this post, we talked about the things you would need to consider when setting up your DMZ’s firewalls and reverse proxy server. We covered NAT-related issues, firewall rules, and firewall architectures.
Looking for a reverse proxy?
JSCAPE MFT Gateway comes with a fully-functional evaluation edition which you can request right now.





