How to install the MFT gateway agent on linux
In this post, we’ll walk you through the steps of installing the JSCAPE MFT Gateway Agent on a Linux machine and adding that agent on MFT Gateway.
‘, ‘‘ ); ?>

 ); ?>/assets/images/image-2.jpeg” alt=”” class=”has-border-color ” style=”border-color:#000208;border-width:1px;border-top-left-radius:0.8rem;border-top-right-radius:0.8rem;border-bottom-left-radius:0.8rem;border-bottom-right-radius:0.8rem”/></figure>
<div class=)
In this post, we’ll walk you through the steps of installing the JSCAPE MFT Gateway Agent on a Linux machine and adding that agent on MFT Gateway.
Delegating network requests to an agent can come in handy if the Linux box running a service you want to create a reverse proxy for is located behind a firewall that doesn’t allow any connections from external sources.

Watch the video
Would you prefer to watch a video version of this tutorial instead? You can play the video below. Otherwise, just skip it if you wish to continue reading.
Before we install the agent software, we need to create login credentials for that agent on the JSCAPE MFT Gateway server. We’ll use those credentials once we start configuring the agent on our Linux machine. To create agent login credentials, just go to the Agents module and click the Add button.

That should bring up the Add Agent dialog. We’ll start by specifying a login name (e.g. agent1) and a password for that login. As usual, we’ll be asked to enter the password twice. So let’s just do that and click Add to proceed.

If everything goes well, we should then see our newly created agent login in the Agents tab.

The next step is to enable the agent service. To do that, we’ll go to the Service tab and click the Edit button…

…and then specify the agent service parameters. These are basically the IP address and port number we want this agent service to listen on also known as the control channel. That will be the same IP address and port number that our active agents will be connecting to.
For this example, let’s just choose 0.0.0.0 for the IP address, which means the agent service will be listening on all available network interfaces, and just leave the port number to its default value, 30025. Let’s just leave the rest as is. In a production environment, though, you will want to replace that example_rsa key with your own key. But for now, let’s just leave that unchanged. Click Save to commit the changes.

At this point, you won’t notice anything yet. That’s because what’s supposed to appear here on this screen are information of our active agents. Since we haven’t installed an agent yet, there’s nothing to display. We’ll get back to this screen once we’ve installed an agent on our Linux machine. That’s what we’re going to do next.

Let’s now head to our Linux machine and install our agent there.
Note: MFT Gateway Agent requires Java to run. If your Linux machine doesn’t have Java on it, you might find this post useful: How To Install Java on Linux. In addition, if you’re using Oracle Java, you may have to install the JCE Unlimited Strength Jurisdiction Policy Files. There’s no need to install those files if you’re using OpenJDK, as it already has them enabled by default.
The first thing is to copy the MFT Gateway Agent Linux installer onto our Linux machine. Now, there are a couple of ways to do this, but, in my case, since I’m connecting to a Linux instance on Amazon EC2 via SSH from my laptop, I can just copy the installer’s download link from the JSCAPE website and run wget with it.
I usually install the agent in the opt directory, so we’ll navigate to that directory first.

Now, we just go to staging.marketing.jscape.com > Products > Managed File Transfer > JSCAPE MFT Gateway > Download > [fill up the form] > click Download
And then once we see the list of installers, we simply copy the link to the MFT Gateway Agent installer. You’ll notice that there are two of them, an rpm and a zip. I’ll just go with the zip file here.

We then go back to our Linux session and run wget with the copied link for the agent installer.
sudo wget {link}
Note: That link might change, so I suggest you follow the steps outlined earlier instead of just copying the link from here.

Once the wget download completes, we look for the newly downloaded file in our current directory and then execute the unzip command with it.
sudo unzip gateway_agent_install.zip

Once the zip file is done unpacking, we then navigate into the JSCAPE MFT Gateway installation directory.
cd JSCAPE_MFT_Gateway_Agent

We then configure our agent so it can connect to that agent service we enabled earlier. To configure the agent, just run the agent-configuration command line utility along with its required parameters:
./agent-configuration -host [ip] -port [port] -user [username] -password [password]
where [ip] and [port] are the control channel IP and port number for the JSCAPE MFT Gateway Server agent service and [username] and [password] are login credentials you will use when connecting to the control channel.
or, in our case, that would be
./agent-configuration -host 172.31.9.252 -port 30025 -user agent1 -password password1
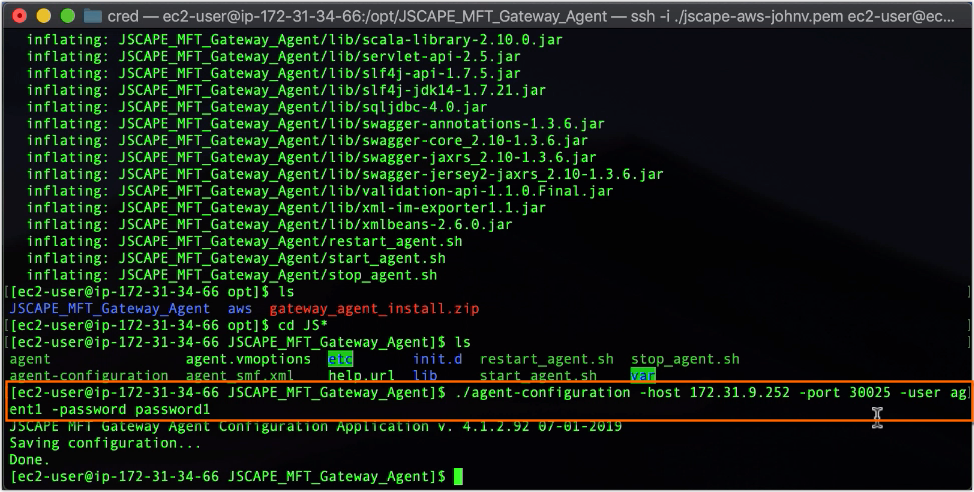
After that, we start the agent by running:
./agent start

Now, we head back to our MFT Gateway Manager Service > Agents > Service tab and, if everything went well, you should then see an entry showing information of the remote agent. For example, you can see its name, the host it’s connecting from, when it started connecting, and how long it’s been up.

That’s it. Now you know how to install JSCAPE MFT Gateway Agent on a Linux machine.
Would you like to try this out yourself? Download a FREE Starter Edition of JSCAPE MFT Gateway now.

 ); ?>/assets/images/image-2.jpeg” alt=”” class=”” style=”border-top-left-radius:0.43rem;border-top-right-radius:0.43rem;border-bottom-left-radius:0.43rem;border-bottom-right-radius:0.43rem”/></figure>
<div class=)
The IT/OT divide: Is your enterprise blind to a critical threat?
Your enterprise security strategy may be incomplete.

 ); ?>/assets/images/image-2.jpeg” alt=”” class=”” style=”border-top-left-radius:0.43rem;border-top-right-radius:0.43rem;border-bottom-left-radius:0.43rem;border-bottom-right-radius:0.43rem”/></figure>
<div class=)
From unplanned downtime to unmatched competitiveness
Why AI is making OT/IT convergence a C-Suite imperative.
