Overview
In the enterprise, servers that receive requests from external clients are often subject to numerous inbound threats. One way to mitigate these threats is to move those servers into the internal network and make them accessible from the outside only through firewalls and a reverse proxy.
A couple of firewalls and a reverse proxy can provide protection by filtering traffic directed at those servers and hiding those servers’ identities. Let’s take a closer look at what I mean.
How a firewall provides protection
Firewalls can filter inbound traffic (it can also filter outbound traffic but we’re not concerned with those here) based on protocols, source/destination IP addresses, source/destination ports, and packet header information specified in the firewalls’ rules and policies.
For example, you can create a rule that would only allow passage to incoming traffic directed at port 22 (SFTP) of a certain server (say Server-2 in the figure below) in your internal network. All connection requests directed at Server-1 and Server-3, as well as requests directed at other ports (e.g. port 21) of Server-2, will be denied.
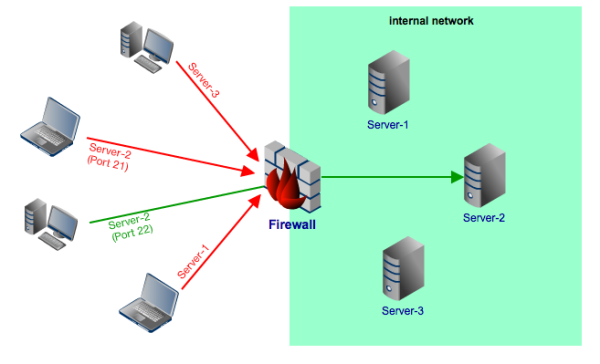
Firewalls and the DMZ
Although an enterprise-class firewall can provide a high level of protection, it would still be very risky if all you have between your internal network and the Internet is a single firewall.
That is why many businesses add another layer of protection in the form of a DMZ. A DMZ is just a network that stands between the Internet and an organization’s internal network. DMZ’s connect to both your internal network and the Internet via one or two firewalls.
The usual practice is to place hosts that serve external clients (e.g. FTP servers, Web servers, mail servers) in the DMZ and prevent access to the internal network.
By limiting access of inbound traffic to the DMZ, you can significantly bring down threats to your internal network.
The problem with this arrangement is that, most of the time, sensitive data end up being stored in the hard disks of those DMZ-based hosts. For some regulations like PCI-DSS, such an arrangement is unacceptable.
Another problem is that, since internal clients may also have a need for the services provided by those servers, another set of those servers are often installed in the internal network. This duplication of servers can be very expensive and administratively demanding (since you may have to keep the data between those two sets of servers consistent).
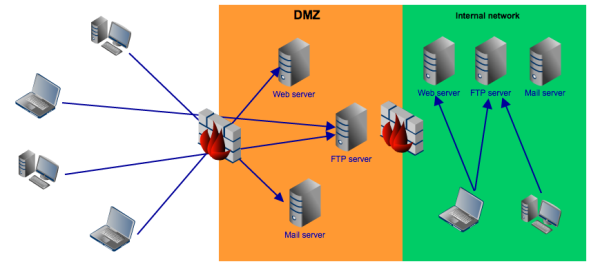
A better solution would be to move all those servers into the internal network and provide external access to them through a server known as a reverse proxy.
How a reverse proxy provides protection
A reverse proxy works by providing services on behalf of servers placed behind it. You can even use it to hide the identity of those servers.
Say, for example, you place an FTP server behind a reverse proxy. An external client will be able to avail of the FTP service by sending its request to the reverse proxy. As soon as the proxy identifies the request to be FTP in nature, it forwards that to the FTP server. The server, in turn, replies through the proxy. All exchanges between the client and the server goes through the reverse proxy.
By hiding the identity of your servers and using a reverse proxy as an intermediary, you make them less vulnerable to attacks.
Just like a firewall, a reverse proxy won’t be able to hold off attacks to your internal network by itself. But when you combine the two, you can arrive at a very strong line of defense.
Here’s the network configuration we recommend:
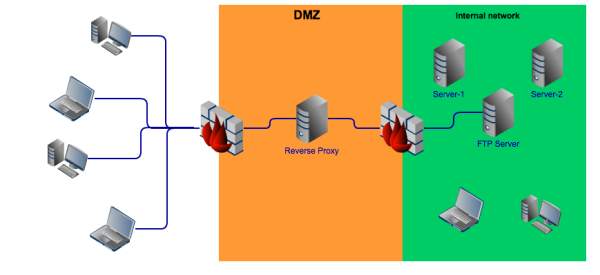
Basically, you place your reverse proxy in the DMZ. The reverse proxy should be set to offer those services you want to share to external clients. In the example shown in the figure above, the service being shared is FTP and nothing else.
Of course, if you want to share more than one service, it would be wise to look for a reverse proxy that already supports multiple services. JSCAPE MFT Gateway, for example, supports FTP, FTPS (FTP over SSL), SFTP/SSH, HTTP, HTTPS, SFTP/SSH and other RAW protocols.
Ideal traffic flow between the Internet and your DMZ
To make sure all incoming traffic are directed to the reverse proxy, you need to place a front-end firewall that denies all packets except those that match these two conditions:
- Their destination address is the IP address or host name of the reverse proxy; and
- The protocol used is FTP. Note, in addition to port 21 make sure to include a passive port range.
If all goes well, all packets that arrive at the reverse proxy will only be those that are requesting for FTP service. As soon as the reverse proxy recognizes them as FTP packets, it will then direct them to the FTP server in the internal network.
Of course, they will have to pass through the back-end firewall. We’ll show you how through your free trial with an account manager.

Ideal traffic flow between your DMZ and your Internal network
The purpose of the back-end firewall is to make sure only legitimate packets go through it and that all of them go straight to the internal FTP server and nowhere else. To enforce this, your back-end firewall should be set to deny all packets except those that satisfy the following conditions:
- Their source address is the IP address or host name of the reverse proxy;
- Their destination address is the IP address or host name of the FTP server; and
- The protocol used is FTP. Note, in addition to port 21 make sure to include a passive port range.
All packets that don’t meet all three conditions are automatically dropped.
Summary
In this post, we talked about firewalls and reverse proxies and how you can set up the two in a DMZ in order to protect your internal network.
Would you like to try a reverse proxy for FREE?
JSCAPE MFT Gateway comes with an evaluation edition which you can request right now.





