Overview
In this tutorial, we’ll show you how to set up automated file transfers wherein a second file is uploaded only if the first upload succeeds.
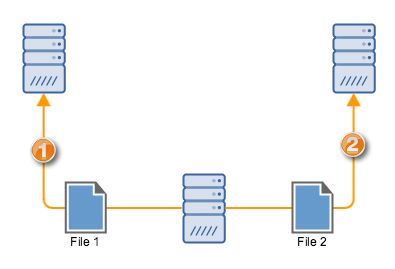
What we want to do
How to do it
To achieve this, we would need two triggers. One trigger would upload the first file, while the second trigger, which should depend on the success of the first upload, will upload the second file.
For this particular example, let’s just assume the first trigger is designed to carry out a scheduled file transfer. Since we already wrote several tutorials for setting up a scheduled file transer, there’s no need to discuss it here. Here are some of those tutorials for reference:
Benefits of a Scheduled File Transfer and How To Set One Up
Scheduling an Automated File Transfer for Files Matching a Regex
How To Set Up A Scheduled Automatic Download With A Trading Partner
Securing Trading Partner File Transfers w/ Auto PGP Encryption & FTPS
How To Get Your MFT Server To Email You About Last Night’s Download
Once you’ve created the trigger that would execute the scheduled file transfer, the next thing would be to create a trigger that listens to the External File Upload trigger event type. This event occurs whenever a file is uploaded as a result of a trigger action.
Because a scheduled file upload is normally the result of a trigger action, then that upload should fire an External File Upload event.
Creating the trigger for the second upload
Let me now walk you through the steps of creating the second trigger.
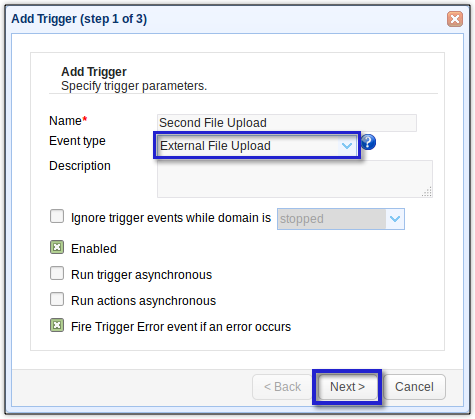
Add a new trigger, give it a descriptive name, and assign it the External File Upload trigger event type. After that, click Next.
In a production environment, you’ll likely have several trigger-initiated uploads. Thus, you would need to customize your second trigger to filter out unrelated uploads. You can do this by adding expressions in the Trigger Conditions dialog.
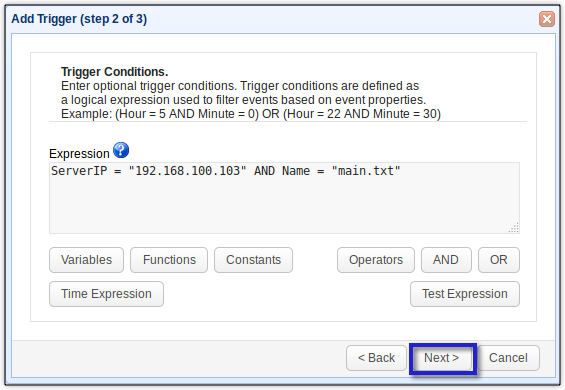
For, example, you can let this trigger act only on a previous upload if the upload was directed at a specific server IP address (say 192.168.100.103) and involved a specific filename (say main.txt). Unless the previously uploaded file was main.txt AND the destination server was 192.168.100.103, this trigger would not proceed. You can find a list of accepted variables, functions, constants, and operators by clicking their respective buttons (see screenshot below).
After entering the expressions, click the Next button.
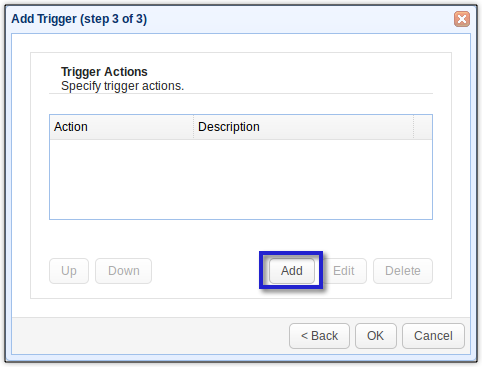
Now it’s time to add the trigger action that would upload the second file. Click the Add button to do that.
Select the file upload trigger action you want to use. There are upload trigger actions for various file transfer protocols. In our case, let’s just use the SFTP File Upload trigger action. Click OK to proceed.
You will then be asked to enter certain parameters such as the destination server’s hostname/IP address, the port number, the user account’s username, that account’s corresponding password, and so on. Fill up the fields with the required values. It’s also at this juncture that you would need to specify the second file you want to upload. Let’s say that file is named “ok.txt”.
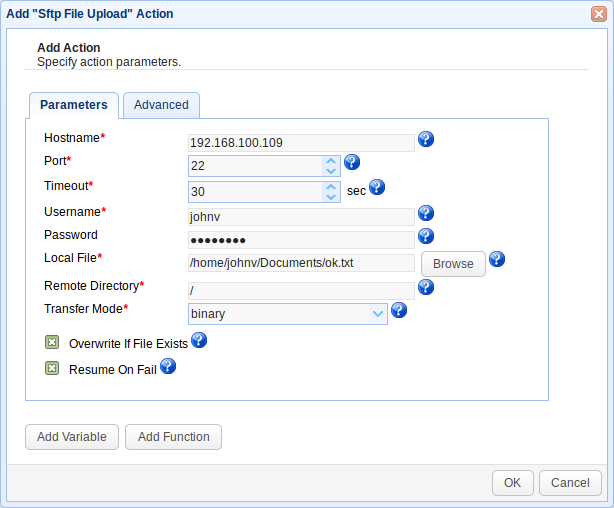
Once you’re done, just click the OK button. You may need to click additional OK buttons until you get back to the main screen. As soon as you’re back at the main screen, don’t forget to click the Apply button to finalize the trigger.
Notice that when entering the trigger action parameters, you could have specified any server you wanted (as long as you have an account on it, of course). Thus, the destination server could have been the same server where the first file was uploaded or it could have been another server.
That’s it.
Think this is too long or too complicated? Here’s a shorter way:
Uploading a 2nd File Only If The 1st Succeeds – Using 1 Trigger
Get Started
This tutorial was created using JSCAPE MFT Server, a managed file transfer server built for secure, automated file transfers. If you’d like to follow the steps on this tutorial but don’t have a running installation of JSCAPE MFT Server, you can download a free, fully-functional evaluation edition now.





