Overview
Last week, while responding to one of the tickets at our HelpDesk, I noticed that the port number used wasn’t standard. While we encounter this quite often, the use of non-standard ports is one of those practices where many IT folks have opposing views.
On one side you have those who consider the use of non-standard ports a form of “security through obscurity” and hence discourage it. On the other, you have those who actually recommend it. Clearly, the topic makes for an interesting discussion, so here we are to discuss it.
Why some people use non-standard ports
Although each network service is assigned a standard port by IANA (Internet Assigned Numbers Authority) – e.g. FTP is normally configured to listen on port 21, HTTP on port 80, and SFTP on port 22 – there are really no hard and fast rules that prohibit the use of other (non-reserved) port numbers.
Related post: Can You Identify The Port Numbers of These 12 File Transfer Protocols?
In fact, most server applications that provide these services will allow you to choose your desired port number. That’s why we sometimes see an FTP service listening on port 2021, a HTTP service on port 8080, or a SFTP/SSH service on port 2222.
Of course, system administrators don’t just use alternative ports simply because they can. In most cases, they do so because:
- The standard port is already in use, or
- They see it as a countermeasure against attacks aimed at the standard port
We’d like to focus more on that second reason, as it’s a classic example of what security folks call “security by obscurity”.
First, let’s define what that is.
What is security through obscurity?
Security through obscurity is that common but highly contentious practice of applying security countermeasures that mainly rely on the confidentiality of an object’s inner workings. For example: you deploy a single-dial padlock that really only requires a single number instead of a combination and then simply bank on the likelihood that no one will know how this special padlock works.
Well, it certainly might fool would-be attackers if its mechanics remain obscure. But for how long?

The thing is, not all attackers are going to be naive. Like, just because a piece of security software is in the form of a binary executable file, doesn’t mean no one would be able to figure out how it actually works. With the right set of tools, a skilled attacker should be able to decompile and reverse engineer the file. Then what?
In the field of cryptography, while private and secret keys are kept confidential, the internal workings of the strongest cryptographic algorithms are actually open to the public. This is so that experts could easily analyse, test, and discover weaknesses. If you attempt to build your own encryption algorithm from scratch and then simply rely on the secrecy of its design, chances are it won’t take much for a highly trained cryptanalyst to break it.
Disadvantages of using nonstandard ports
Let’s now go back to our discussion of using nonstandard ports. Well, first of all, if you use nonstandard ports for your network services, your end users might have problems connecting to them. For example, if you use 8080 instead of 80 for your HTTP web file transfer service, likeso:
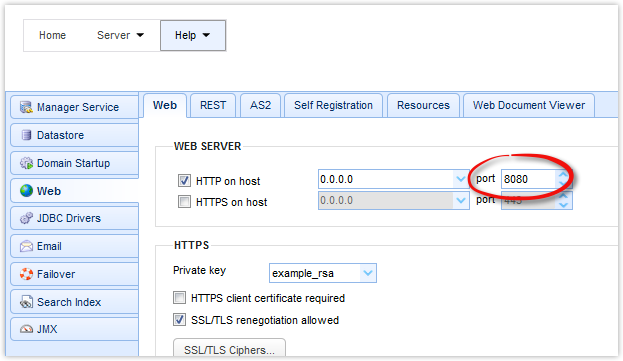
all your users will have to include the 8080 port number when they enter your site’s URL in their browser. Otherwise, they won’t be able to connect because browser’s are only configured to (inconspicuously) insert port 80 by default.
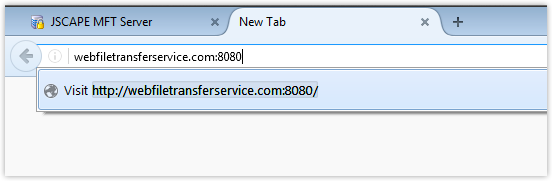
You might also encounter issues when setting up the firewalls, NATs, routers, and other network devices your end users would have to pass through to get to your services.
Furthermore, if we go by the argument against “security by obscurity”, then it’s easy to see why some people in the security community don’t recommend it. As a security countermeasure, nonstandard ports can only do so much.
They might be effective against reconnaissance scans aimed at discovering IP addresses that might be running commonly used network services. (The article “How to Detect Rogue FTP Servers on your Network” offers a good example of these types of scans.). However, they won’t be able to prevent a dedicated hacker or APT (advanced persistent threat) from finding openings in your system.
Still, while not all attackers are script kiddies, not all are elite hackers either.
Why it might not be as bad as others paint it to be
One widely accepted principle in information security is that which employs multiple layers (of security), better known as defense-in-depth. The more layers you have, the more effective your network will be in mitigating a wider range of threats.
It’s similar to the way filtration systems remove impurities from drinking water. They don’t go straight to filtering out the tiniest, deepest-penetrating microbes. Similarly, nonstandard ports provide a way of filtering out one group of attackers. They can, for instance, render basic recon scans ineffective.
Again, they won’t be able to stop a highly targeted attack. If the hacker already knows exactly which server to attack and simply needs to find a specific service by checking every single port on that server, then a nonstandard port won’t be able to offer much resistance. Note, however, that in scanning every single port on the server, that attacker is bound to trigger alarms bells in an IDS.
Hence, in the spirit of defense-in-depth, you will want to employ nonstandard ports as a countermeasure alongside other, relatively stronger countermeasures, like:
- password policies (ex: read the post “Protecting FTP Passwords from Brute Force Attacks“),
- auto-blocking IPs after x-number of failed connection attempts ,
- two-factor authentication,
- applying the latest patches and updates,
- IP and MAC-based filtering,
- deploying Intrusion Detection and Prevention Systems (IDS/IPS),
- and others
Simply put, the use of nonstandard ports doesn’t necessarily equate to poor security. Just don’t use it alone.
Next Steps
JSCAPE MFT Server comes with strong authentication, data-at-rest encryption, data loss prevention (DLP), malware protection, high availability, and many more features to support flexible, reliable and secure file transfer operations.
A file transfer solution with extensive security capabilities will help you meet stringent security policies and regulatory compliance requirements. >> Request your risk-free trial here.





