Files you upload to an Amazon S3 trading partner through JSCAPE MFT Server are normally stored in plaintext. If you want to encrypt those files to minimize the risk of a data breach, one way to do that is by using AES-256 Amazon S3 server-side encryption. We’ll show you how to use this particular service in this post; and if you want to request a free trial, click here.
Watch the video
Would you prefer to watch a video version of this tutorial instead? You can play the video below. Otherwise, just skip it if you wish to continue reading.
[On AWS S3
To use Amazon S3 AES-256 enryption, the first thing you need to do is navigate to the S3 service.
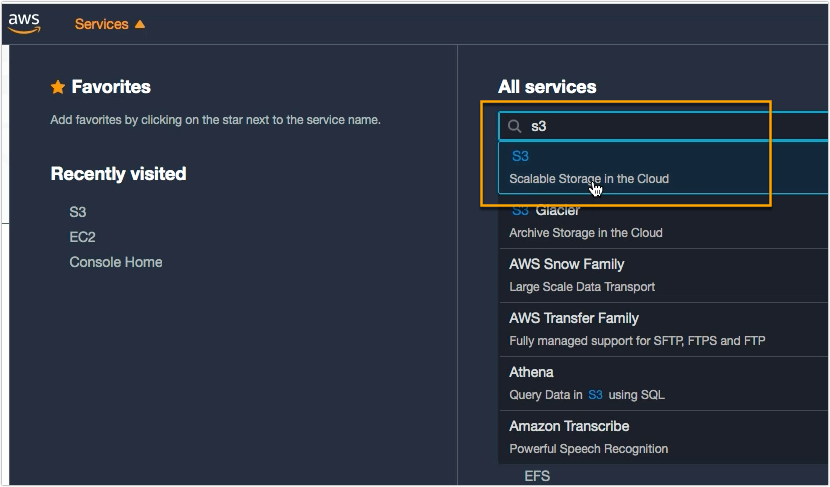
Go to the bucket that you want to secure with AES 256 encryption.
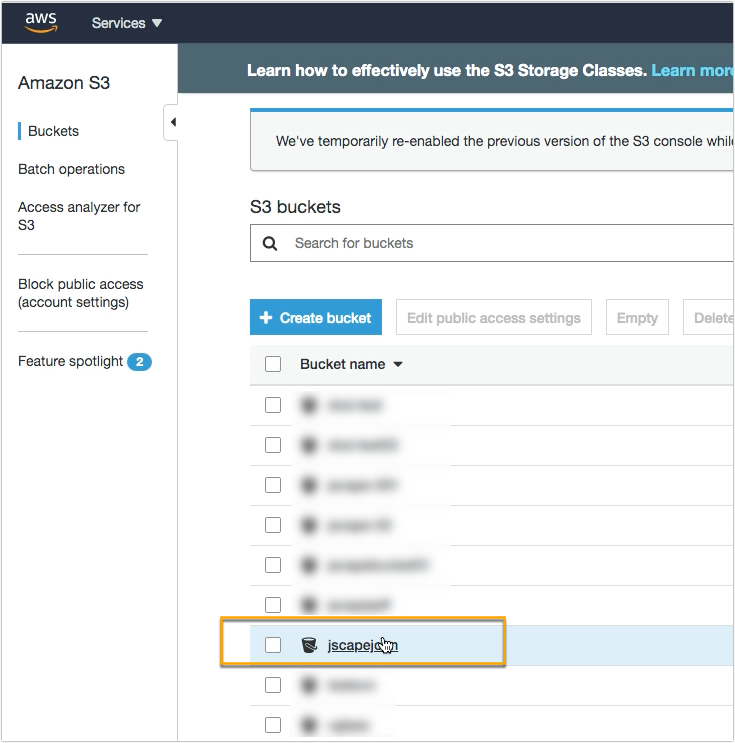
In my case, I have a folder named ‘folder1’ inside my Amazon S3 bucket. Let’s take note of that, as that’s where I’m going upload files from my JSCAPE MFT Server instance.

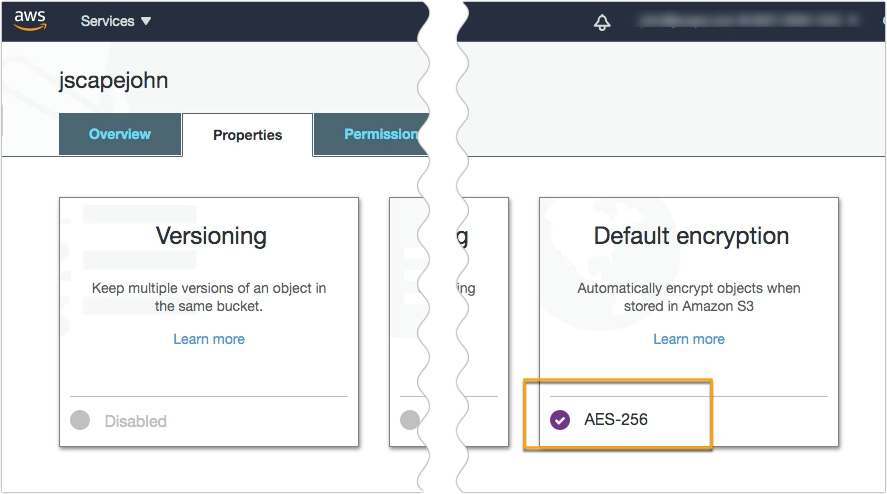
Once you’re inside your S3 bucket, navigate to the Properties tab and go to the Default encryption section. Most likely, it will be marked as Disabled. Meaning, no encryption is currently used. Click that Disabled label to edit the default encryption setting.

Next, select AES-256 as your default encryption and then click Save.

That Disabled label you saw earlier should now be replaced with AES-256. That means, any file you upload to this S3 bucket moving forward will already be encrypted with Amazon S3 AES-256 encryption.
[On JSCAPE MFT Server]
Now that we have AES-256 enabled on our S3 bucket, let’s now head over to our JSCAPE MFT Server instance to configure it so it can start using S3 server-side encryption when it uploads files to that S3 bucket.
Go to the domain where you have your S3 trading partner object…

… and edit that S3 trading partner.
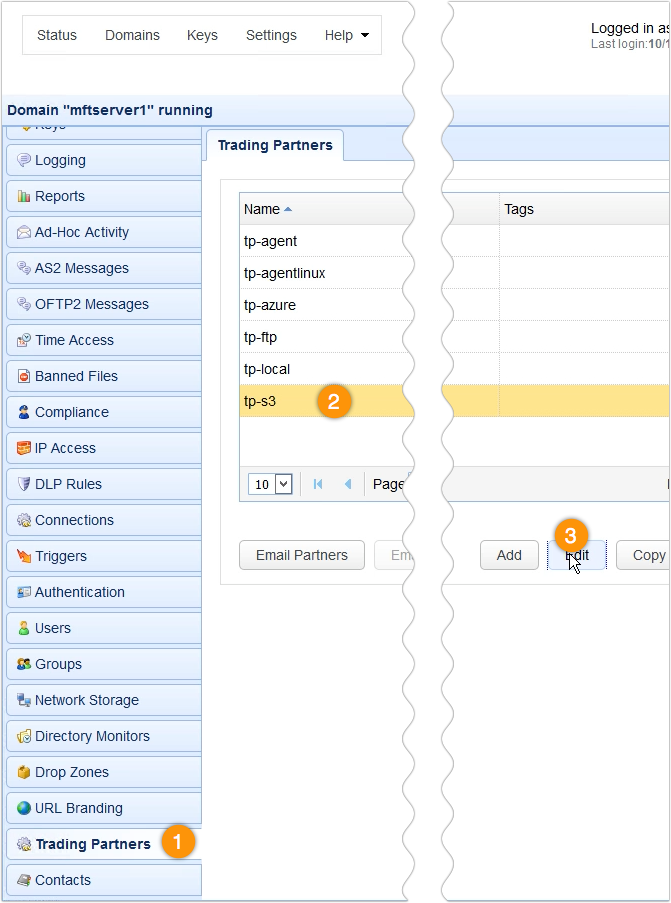
Scroll down to the Authentication section and then click the Use encryption checkbox.
Select the AES-256 option and then click the OK button.

With that, this S3 trading partner should now be ready to use S3 AES-256 encryption.
That’s all there is to it.
Before we end, let me just show you what happens when you upload a file to your AES-256-protected Amazon S3 bucket from JSCAPE MFT Server.
What I have here is a trigger that uploads a file to my Amazon S3 bucket.

So, as you can see, the Partner setting is set to tp-s3, which is the name of my Amazon S3 trading partner object. In addition, the file this trigger is configured to upload is named file01.txt, and it’s going to be uploaded to the folder named ‘folder1’ under the S3 bucket named ‘jscapejohn’.

So, if I run this trigger…

… and check inside the S3 bucket folder named folder1 through the AWS Management Console, I should see the newly uploaded file named file01.txt. If I click on that file and check its properties, I see that it has indeed been encrypted with AES-256 encryption.
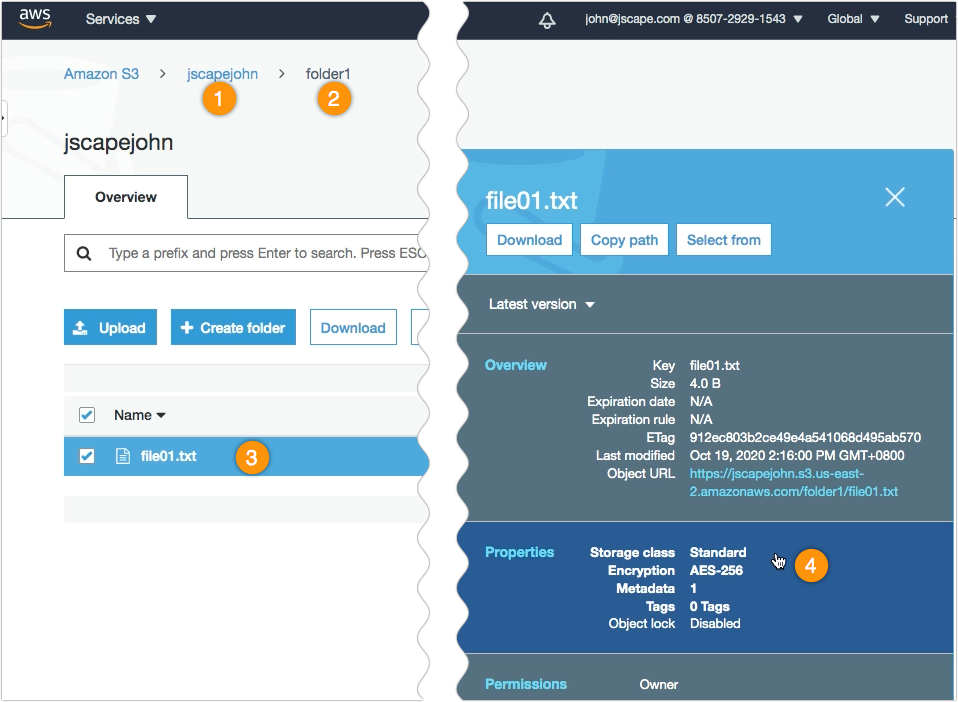
That’s it. Now you know how to use AWS S3 AES-256 to encrypt files uploaded to your S3 trading partner using JSCAPE MFT Server.
Get started
Want to try this out? Request the freetrial of JSCAPE MFT Server now.
Related content
Using AWS KMS To Encrypt Files You Upload To Your S3 Trading Partner
What is AES Encryption & How Does it Work?
How To Copy Data From Azure To AWS S3 | JSCAPE
How to Download Newly Added Files from an AWS S3 Folder
How To Schedule Automated File Uploads From Your Server To Box Cloud Storage
How To Use Amazon S3 As The File Storage System of Your MFT Server





